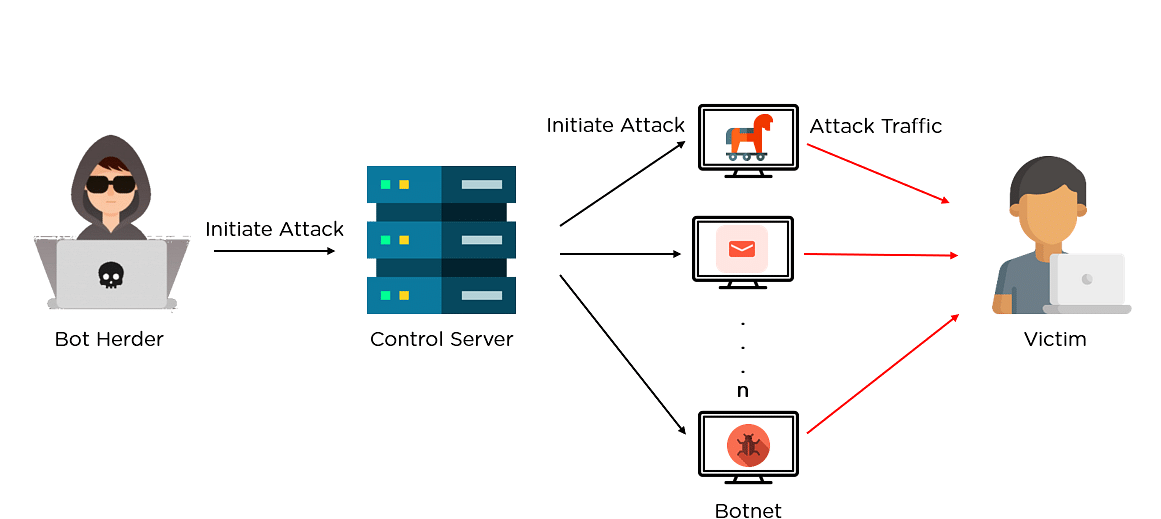
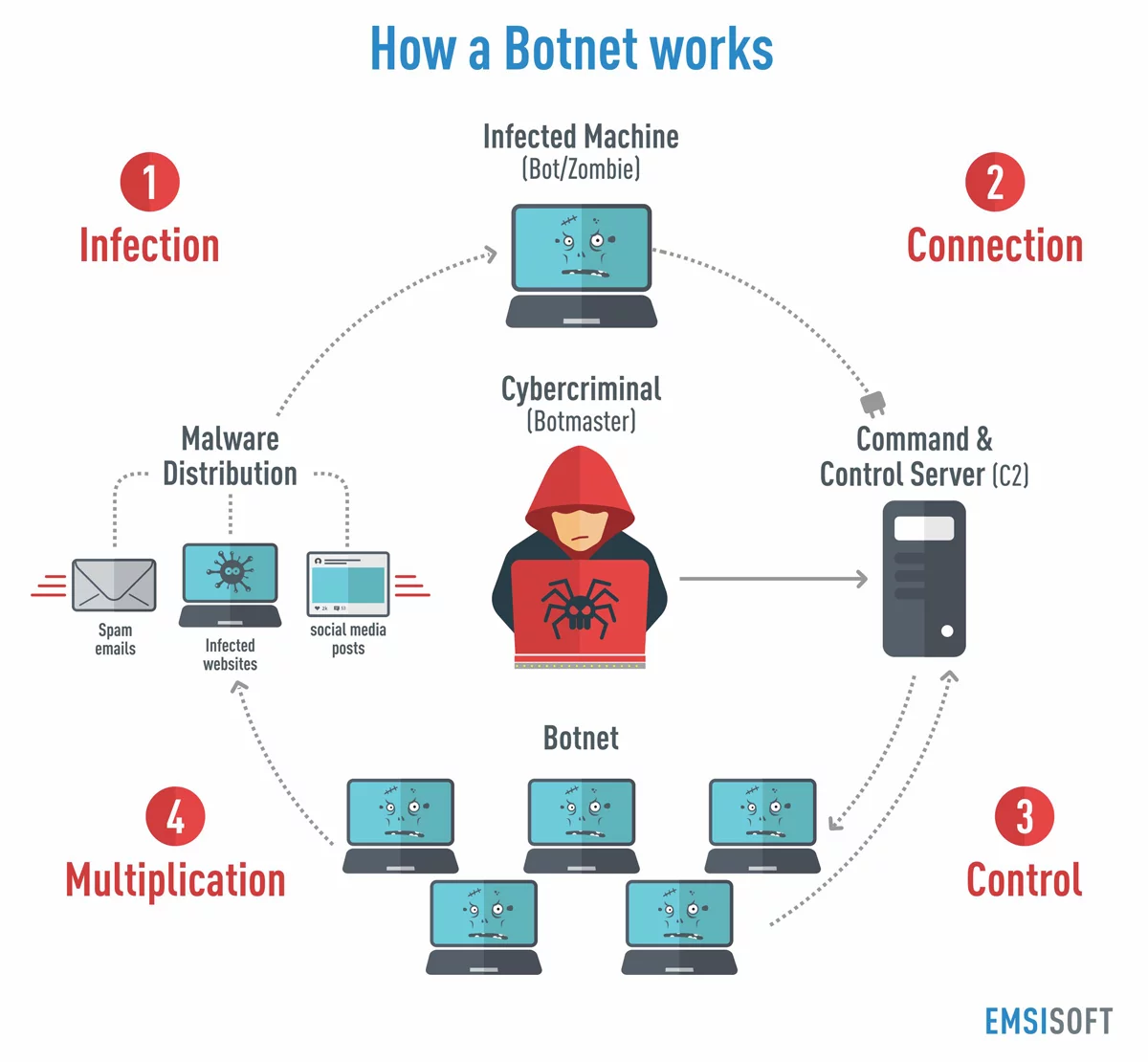
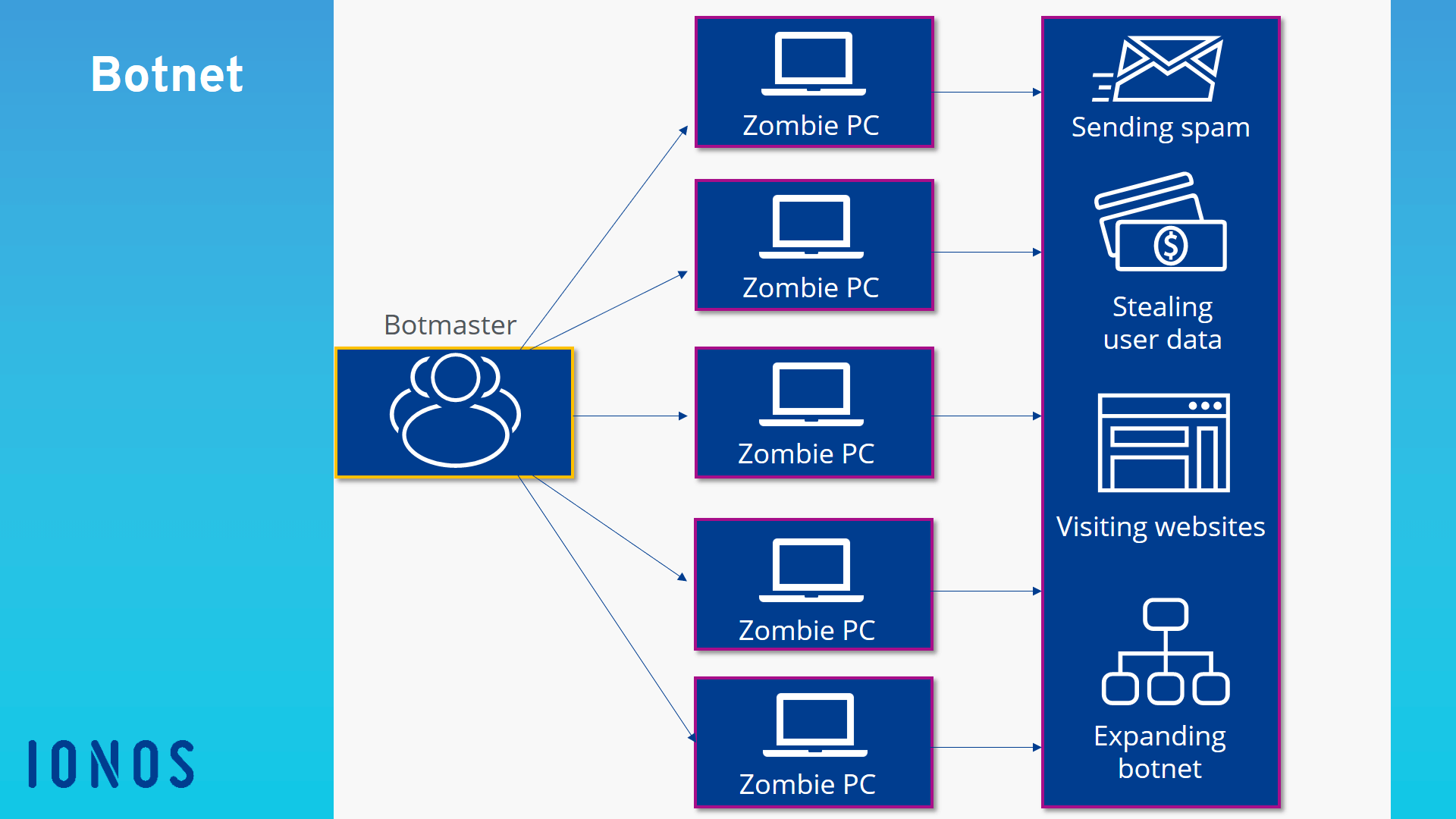
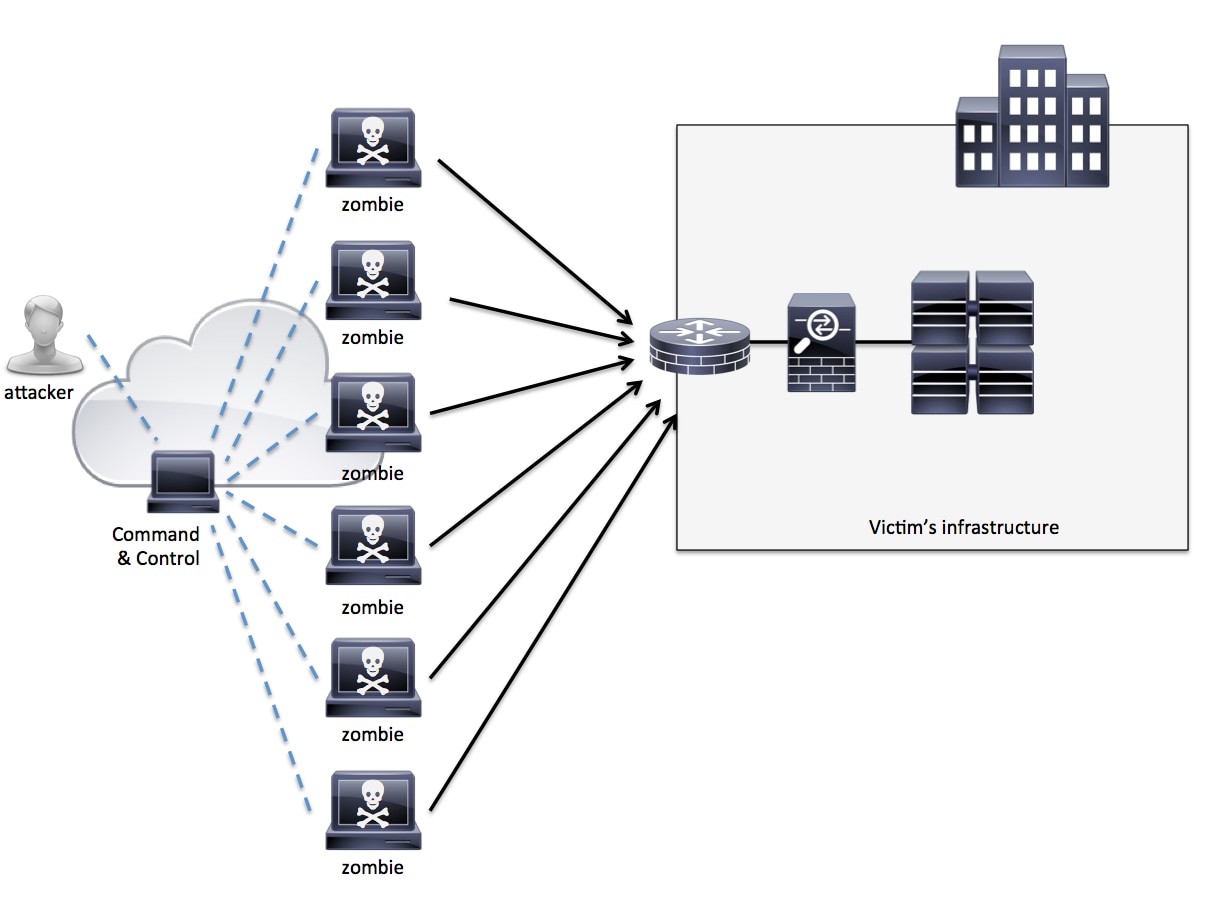
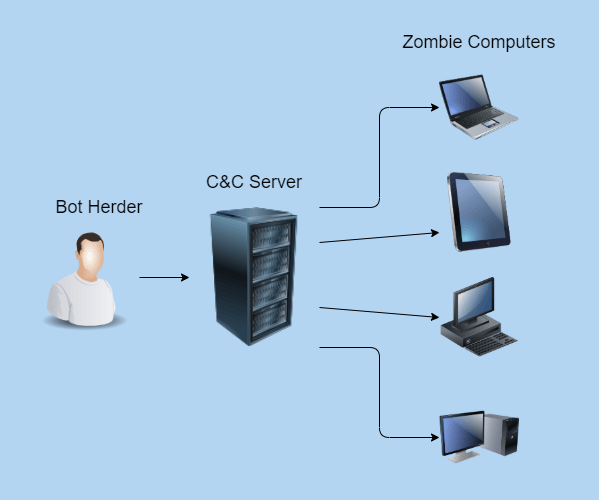
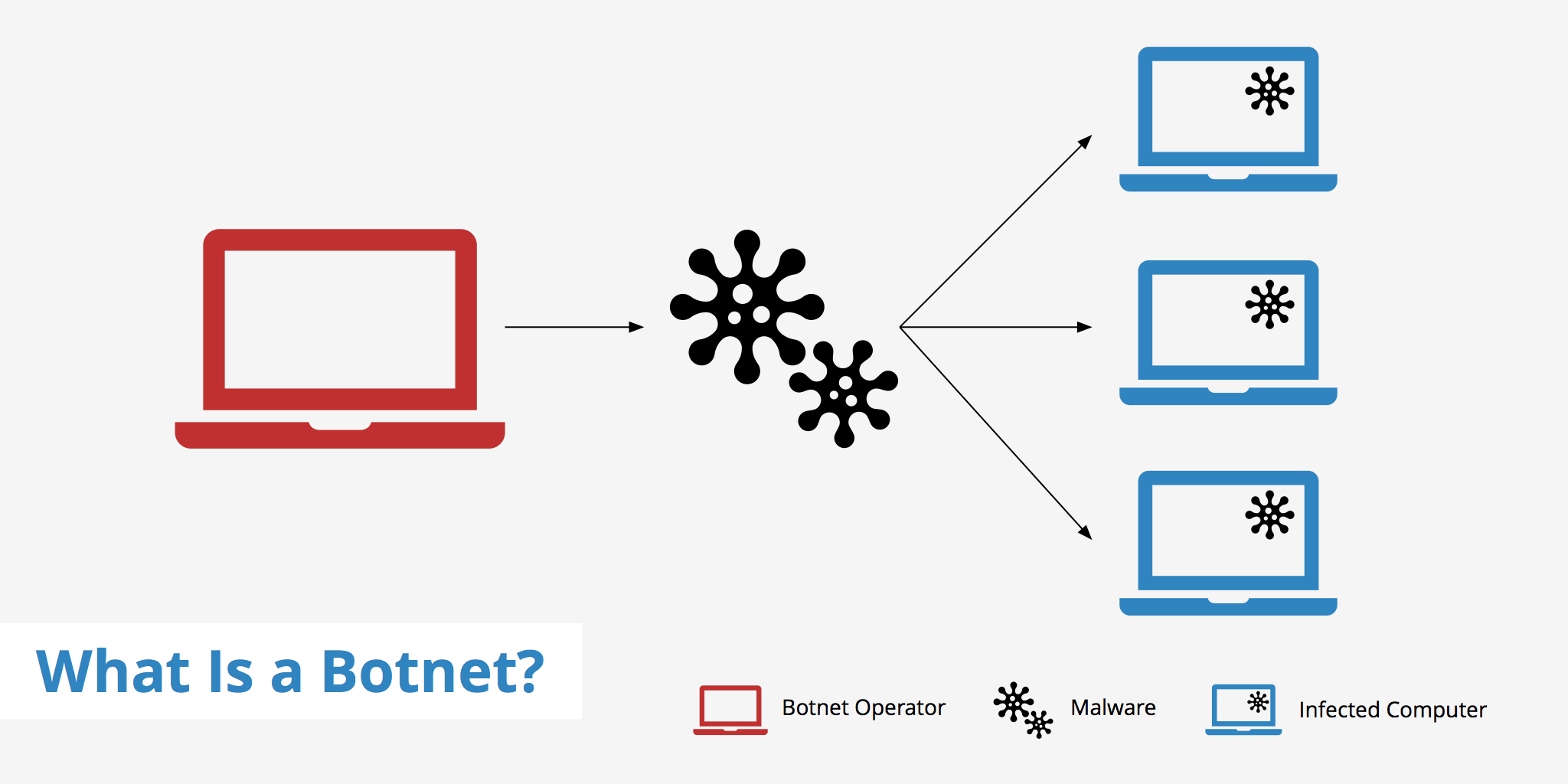
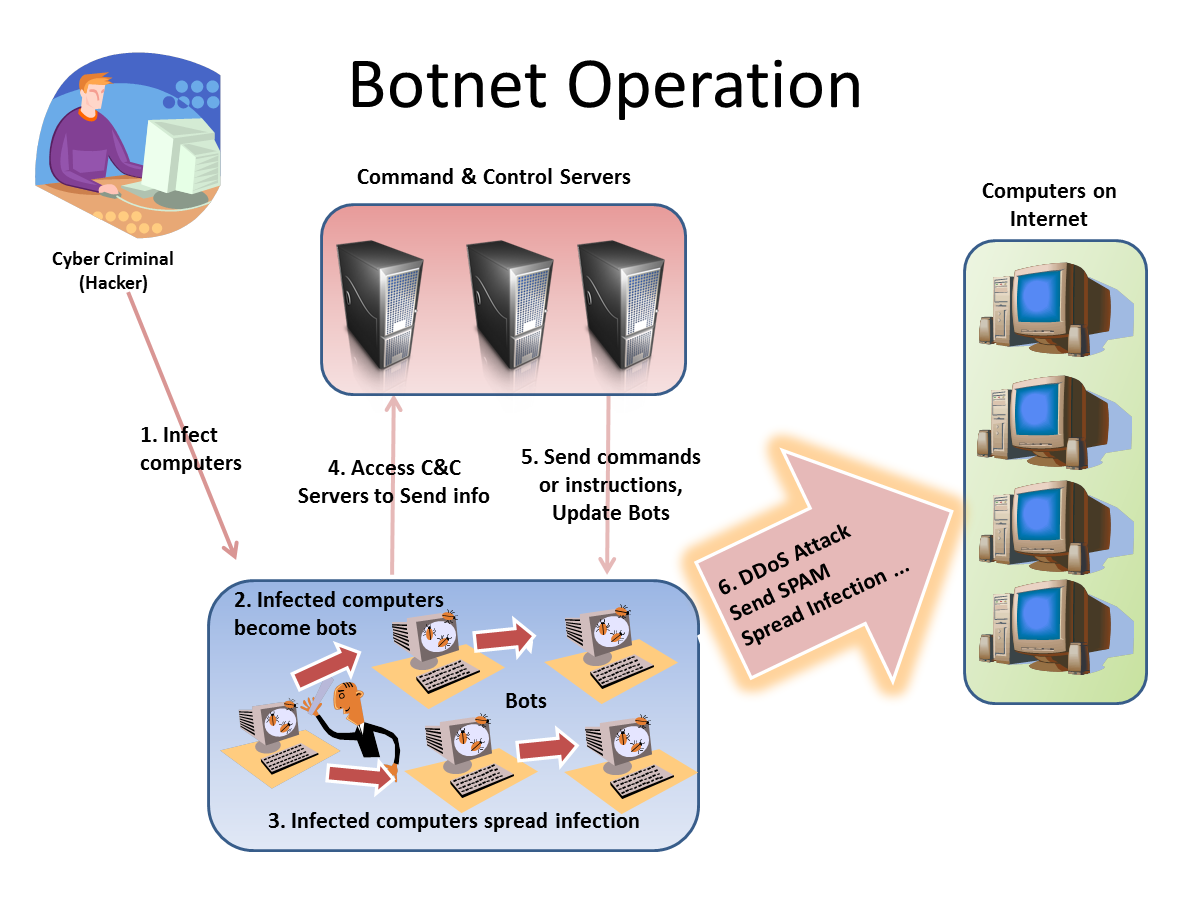
What Central Component Is Necessary To Form A Botnet - The botmaster typically controls the botnet through a. A botmaster or bot herder (botnet herder) is the hacker that organizes the botnet attacks. Web a botnet is a network of devices (known as “bots” or occasionally “zombies”) that a hacker controls remotely. Web a botnet (short for “robot network”) is a network of computers infected by malware that are under the control of a single. A command and control (c&c) server is the central computer that cybercriminals use to communicate with all other infected devices. Web in one breadth sense, that’s exactly thing botnets exist: What is it called when a fraudulent email masquerades as a legitimate communication in an attempt to get a user to reveal sensitive information? Web a botnet is mainly made up of two major components: Web what central component is necessary to form a botnet? Compromised computers are also called zombies or.
Anatomy of a NCTA — The & Television Association
Command & control server (c&c) what is it called when a fraudulent email. Web a botnet is a collection of hosts under the control of a botmaster. The botmaster typically controls the botnet through a. Command & control (c&c) server dns server transformer ethernet switch. The term “botnet” refers to a collection of computers linked together to perform a specific.
What Is a and How Does It Work? Simplilearn
P2p botnet structures make it harder for law enforcement to locate any centralized source. Web a network of compromised computers is called a botnet. Web the main component of the botnet is depicted in figure 1, the four main components are botmaster, infected host. Web what central component is necessary to form a botnet? A botmaster or bot herder (botnet.
Security+ Course 1.1 Malware SPK Tech Fit
A command and control (c&c) server is the central computer that cybercriminals use to communicate with all other infected devices. A network of robots used to commit cyber crime. The botmaster typically controls the botnet through a. Web a botnet is a collection of hosts under the control of a botmaster. What central component is necessary to form a botnet?
What are and how can you protect yourself from them? IONOS
Web what central component is necessary to form a botnet? Web what central component is necessary to form a botnet? Web in a p2p botnet, each infected device functions as a client and a server. Command & control (c&c) server dns server transformer ethernet switch. Command & control (c&c) server ethernet switch dns.
How To Build A
Web the main component of the botnet is depicted in figure 1, the four main components are botmaster, infected host. Compromised computers are also called zombies or. A network of robots used to commit cyber crime. Command & control (c&c) server dns server transformer ethernet switch. A botmaster or bot herder (botnet herder) is the hacker that organizes the botnet.
A Cisco Guide to Defending Against Distributed Denial of Service
Botnets are networks of hijacked computer devices used to carry out various scams and cyberattacks. Web a botnet consists of four key components: Command & control server (c&c) what is it called when a fraudulent email. Web a botnet is a network of devices (known as “bots” or occasionally “zombies”) that a hacker controls remotely. What central component is necessary.
Bot Attacks Are Increasingly Targeting Businesses. How to Stay Safe
A botnet is malicious software that hackers use to apply denial of service dos attacks. Web in a p2p botnet, each infected device functions as a client and a server. Web a botnet is a network of devices (known as “bots” or occasionally “zombies”) that a hacker controls remotely. Botnets are networks of hijacked computer devices used to carry out.
What Is a KeyCDN Support
A botnet is malicious software that hackers use to apply denial of service dos attacks. Web how do botnets work? Web a botnet is mainly made up of two major components: What is it called when a fraudulent email masquerades as a legitimate communication in an attempt to get a user to reveal sensitive information? A botmaster or bot herder.
Massive System Tied To Wordpress Attacks HealthGuard Cyber
Ethernet switch command & control (c&c) server dns. The bots are the infected machines that a botmaster. Web what central component is necessary to form a botnet? The term “botnet” refers to a collection of computers linked together to perform a specific task. A network of robots used to commit cyber crime.
Viruses, Trojans, and worms, oh my The basics on malware Ars Technica
Web a network of compromised computers is called a botnet. Command & control (c&c) server dns server transformer ethernet switch. Compromised computers are also called zombies or. Web a botnet is mainly made up of two major components: Web a botnet is a collection of hosts under the control of a botmaster.
P2p botnet structures make it harder for law enforcement to locate any centralized source. Web the main component of the botnet is depicted in figure 1, the four main components are botmaster, infected host. Web a botnet (short for “robot network”) is a network of computers infected by malware that are under the control of a single. To better understand how botnets functions, considered ensure the name itself is an. A botnet is malicious software that hackers use to apply denial of service dos attacks. Command & control (c&c) server ethernet switch dns. Web how do botnets work? The bots are the infected machines that a botmaster. Web what central component is necessary to form a botnet? The term “botnet” refers to a collection of computers linked together to perform a specific task. Web what central component is necessary to form a botnet? Compromised computers are also called zombies or. Web in one breadth sense, that’s exactly thing botnets exist: Web what component is necessary to form a botnet? Command & control (c&c) server dns server transformer ethernet switch. Web in a p2p botnet, each infected device functions as a client and a server. Web a botnet is a network of devices (known as “bots” or occasionally “zombies”) that a hacker controls remotely. The botmaster typically controls the botnet through a. A network of robots used to commit cyber crime. Web a network of compromised computers is called a botnet.
What Is It Called When A Fraudulent Email Masquerades As A Legitimate Communication In An Attempt To Get A User To Reveal Sensitive Information?
Individual bots have a list of other infected devices and will seek them out to update and to transmit information between them. Web in a p2p botnet, each infected device functions as a client and a server. Web what central component is necessary to form a botnet? Web how do botnets work?
The Term “Botnet” Refers To A Collection Of Computers Linked Together To Perform A Specific Task.
Botnets are networks of hijacked computer devices used to carry out various scams and cyberattacks. A centralized model with direct. Web what component is necessary to form a botnet? Command & control (c&c) server dns server transformer ethernet switch.
Web A Botnet Consists Of Four Key Components:
What central component is necessary to form a botnet? A botmaster or bot herder (botnet herder) is the hacker that organizes the botnet attacks. The bots are the infected machines that a botmaster. Command & control server (c&c) what is it called when a fraudulent email.
Web In One Breadth Sense, That’s Exactly Thing Botnets Exist:
Web the main component of the botnet is depicted in figure 1, the four main components are botmaster, infected host. Web what central component is necessary to form a botnet? Ethernet switch command & control (c&c) server dns. Web a network of compromised computers is called a botnet.