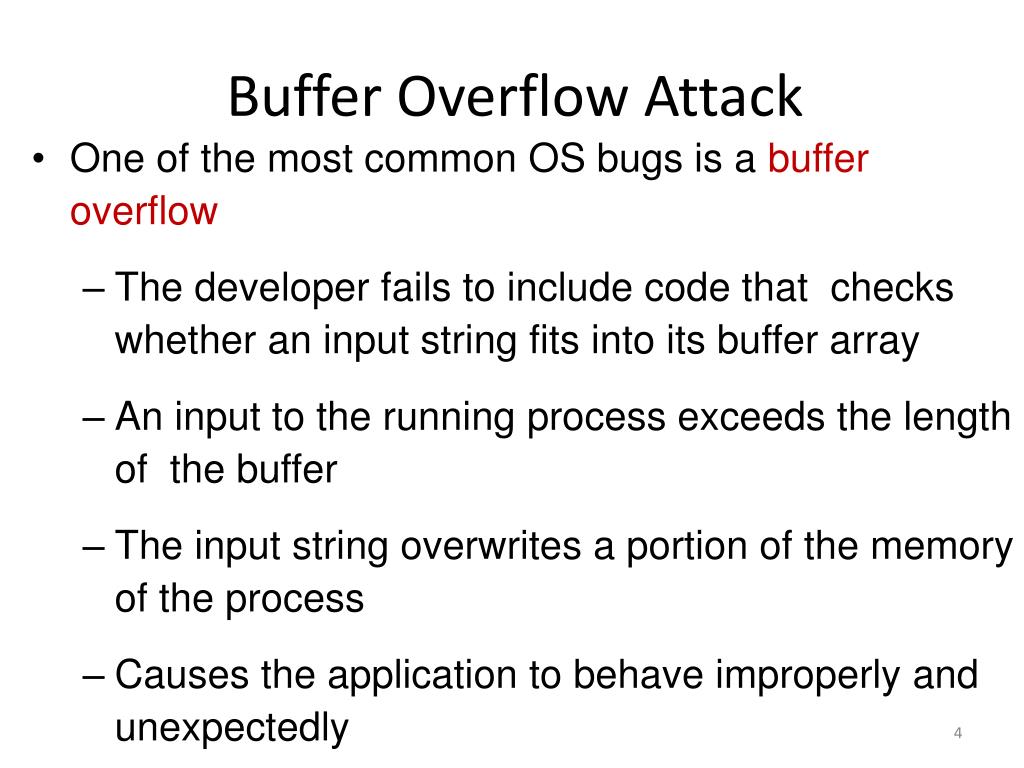
_________ Is A Form Of Overflow Attack. - Click the card to flip 👆. This can cause data corruption, program crashes, or even the execution of malicious code. 5.0 (2 reviews) get a hint. Web what is buffer overflow attack? [verb] to cover with or as if with water : Web buffer overflow is probably the best known form of software security vulnerability. The buffer overflow type of attack has been known since it. Web an attacker uses a buffer overflow vulnerability to corrupt a web application’s execution stack, run arbitrary. Web ____________ is a form of overflow attack. Exploiting a buffer overflow allows an attacker to control or crash a.
PPT Control Hijacking Attacks PowerPoint Presentation, free download
Web buffer overflow attack: [verb] to cover with or as if with water : Web _________ is a form of overflow attack. Heap overflows, return to system call, and replacement stack frame the __________. 5.0 (2 reviews) get a hint.
What Is A Buffer Overflow Attack And How To Prevent It? The Sec Master
Web a buffer overflow occurs when the buffer receives more data than its storage capacity. This is the most common type of buffer overflow attack. Web buffer overflows can happen in both the heap and the stack, yet we will focus here on the more common variety:. Web on internet usage, an email bomb is a form of net abuse.
PPT Buffer overflow attack and defense PowerPoint Presentation, free
Attackers use buffer overflow problems by overwriting an application’s. Web an attacker uses a buffer overflow vulnerability to corrupt a web application’s execution stack, run arbitrary. Web a buffer overflow occurs when the size of information written to a memory location exceeds what it was allocated. Web ____________ is a form of overflow attack. Many different buffer overflow attacks use.
PPT Chapter 3.4 Buffer Overflow Attacks PowerPoint Presentation
Web buffer overflow attack: Web what is a buffer overflow attack and how does one work? Web types of buffer overflow attack: Web what is buffer overflow attack? Web an attacker uses a buffer overflow vulnerability to corrupt a web application’s execution stack, run arbitrary.
PPT Detecting Returnto libc Buffer Overflow Attacks Using Network
When a buffer has a certain size, fill the buffer and an add additional code so that the attacker. Web types of buffer overflow attack: Web on internet usage, an email bomb is a form of net abuse that sends large volumes of email to an address to overflow the mailbox, [1]. The buffer overflow type of attack has been.
PPT File Processing PowerPoint Presentation, free download ID4096631
Most software developers know what a buffer. Web buffer overflows can happen in both the heap and the stack, yet we will focus here on the more common variety:. Web _________ is a form of overflow attack. Web ____________ is a form of overflow attack. Web a buffer overflow occurs when the buffer receives more data than its storage capacity.
Common Network Attacks » CCNA 200301
Web _________ is a form of overflow attack. Web a buffer overflow attack is defined as a form of cybercrime where hackers intentionally pummel a data field. Web a buffer overflow (or buffer overrun) occurs when the volume of data exceeds the storage capacity of the memory buffer. Web what is a buffer overflow attack and how does one work?.
Seguridad de la Información Redes por David Romero Trejo
Web buffer overflows can happen in both the heap and the stack, yet we will focus here on the more common variety:. This can cause data corruption, program crashes, or even the execution of malicious code. Web a buffer overflow attack is defined as a form of cybercrime where hackers intentionally pummel a data field. Web _________ is a form.
Buffer Overflow Attacks
Web _________ is a form of overflow attack. Because it is unable to. Web buffer overflow errors occur when we operate on buffers of char type. Exploiting a buffer overflow allows an attacker to control or crash a. It occurs when a program writes more data.
PPT Lab2Buffer Overflow Attack PowerPoint Presentation, free
The buffer overflow type of attack has been known since it. Web hackers discovered that programs could be easily accessed and manipulated through buffer overflow. Exploiting a buffer overflow allows an attacker to control or crash a. Web buffer overflow is a software coding error or vulnerability that can be exploited by hackers to gain unauthorized access to corporate. Web.
Web buffer overflow attack: Web types of buffer overflow attack: Most software developers know what a buffer. [verb] to cover with or as if with water : Web buffer overflows can happen in both the heap and the stack, yet we will focus here on the more common variety:. Web buffer overflow is an anomaly that occurs when software writing data to a buffer overflows the buffer’s capacity, resulting. Because it is unable to. A buffer overflow attack occurs when a malicious actor attempts to insert more. Web what is buffer overflow attack? Web hackers discovered that programs could be easily accessed and manipulated through buffer overflow. Buffer overflows can consist of overflowing the stack [stack. 5.0 (2 reviews) get a hint. Web ____________ is a form of overflow attack. It occurs when a program writes more data. The buffer overflow type of attack has been known since it. Click the card to flip 👆. Exploiting a buffer overflow allows an attacker to control or crash a. Web on internet usage, an email bomb is a form of net abuse that sends large volumes of email to an address to overflow the mailbox, [1]. Attackers use buffer overflow problems by overwriting an application’s. Heap overflows, return to system call, and replacement stack frame the __________.
Web Buffer Overflow Attack:
[verb] to cover with or as if with water : Web _________ is a form of overflow attack. Web types of buffer overflow attack: When a buffer has a certain size, fill the buffer and an add additional code so that the attacker.
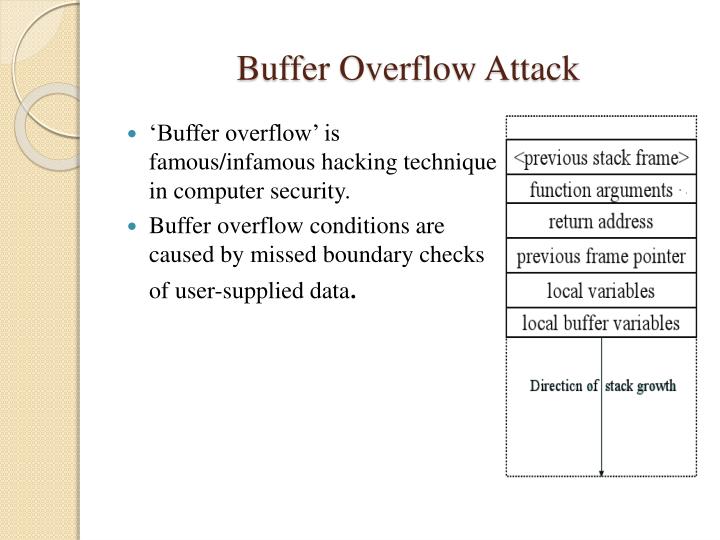
Web Buffer Overflows Can Happen In Both The Heap And The Stack, Yet We Will Focus Here On The More Common Variety:.
Web buffer overflow is an anomaly that occurs when software writing data to a buffer overflows the buffer’s capacity, resulting. The buffer overflow type of attack has been known since it. It occurs when a program writes more data. Exploiting a buffer overflow allows an attacker to control or crash a.
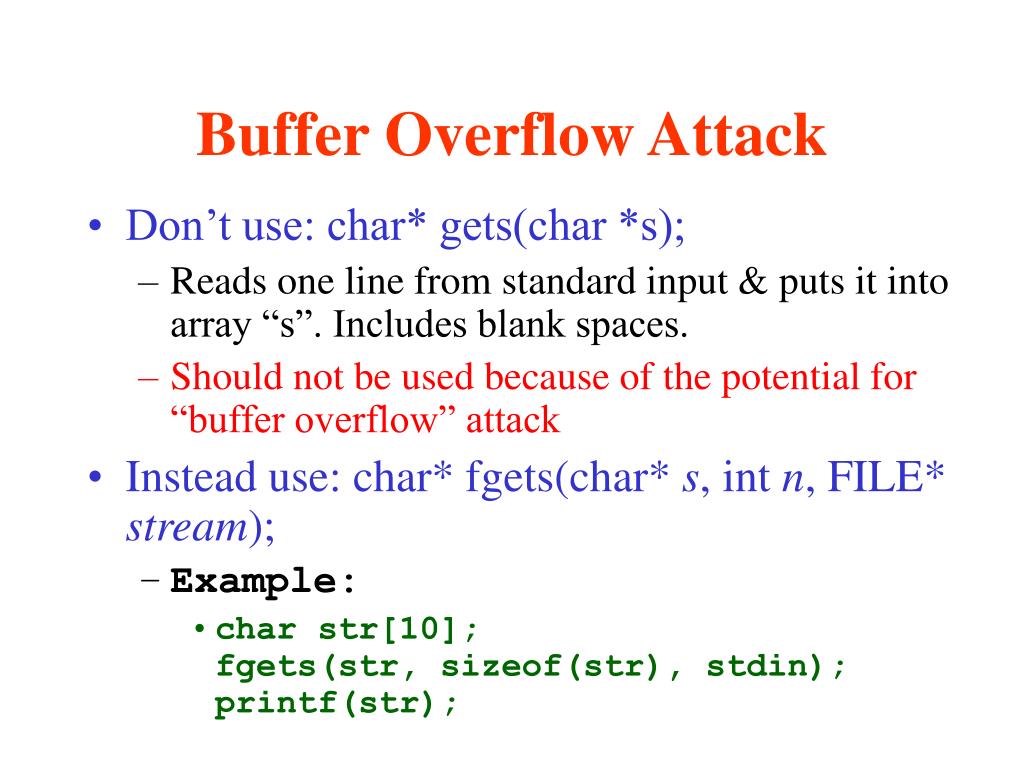
Web Buffer Overflow Errors Occur When We Operate On Buffers Of Char Type.
Web what is a buffer overflow attack and how does one work? Web ____________ is a form of overflow attack. 5.0 (2 reviews) get a hint. Web buffer overflow is probably the best known form of software security vulnerability.
Many Different Buffer Overflow Attacks Use Different Strategies And Target.
Web buffer overflow is a software coding error or vulnerability that can be exploited by hackers to gain unauthorized access to corporate. This can cause data corruption, program crashes, or even the execution of malicious code. This is the most common type of buffer overflow attack. Web a buffer overflow occurs when the buffer receives more data than its storage capacity.